
Elitism: a plight of information security
Information security will likely never stop growing. Every year, we see new sophisticated attack utilized by all kinds of threat actors. Development and distribution of hacking tools obliterate the otherwise steep learning curve and barrier to entry, allowing anyone with a grudge to simply point their tool at someone they don’t like and potentially cause significant disruption. This was observed to be even more on the rise with digital ecosystem changing during the pandemic. More workplaces implemented a Work-From-Home solution, which meant that employees’ digital security in their homes now could have a noticeable impact on the safety of the company.
Phishers gleefully seized the opportunity to use a topic most everyone on earth would be both interested in and worried about. As seen in Microsoft’s Digital Defense Report, phishing attacks skyrocketed with Covid (See Figure 1). And they worked.
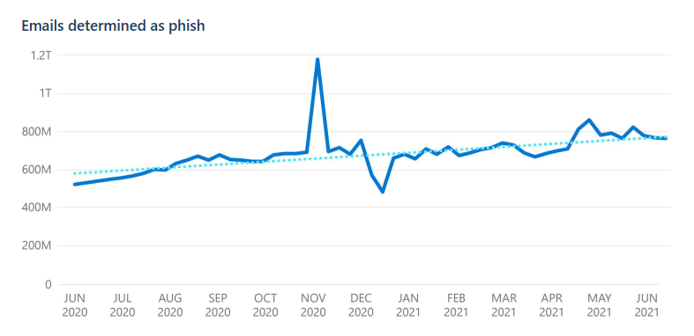
Figure 1: Emails determined as phishing email Source: Microsoft Digital Defense Report
Why?
Well, other than the logistical opportunity presented by the pandemic, attacking the human element has always been effective and simple. While new tools are developed and new vulnerabilities discovered by highly sophisticated researchers, social engineering has mostly stayed the same in attack vector and method – because it works. No matter how well the mitigation and remediation match the opposition’s growth, human error and human exploits remain the same.
But information security as a community has developed a strangely toxic and elitist culture (beyond the gatekeeping against women in the field). Users are shamed for falling for deception tactics that have worked for decades – tactics that are designed to manipulate the user by instilling a distressed emotional state and then leveraging the lapse of judgement. Mistakes happen – to everyone. Information security experts can fall or phishing emails if caught on the wrong day or the wrong time.
Shaming users will make them less likely to want to own up to the mistake made and creates an unhealthy environment, which itself might spawn a negative loop of mistakes. The elitism and idea that we as information security professionals are better than the users is unhealthy for everyone involved – not to mention how it makes it more difficult for new blood to enter the scene.
The consequences of a user clicking a phishing mail and infecting their device can be mitigated. By practicing Defense-in-Depth, Zero Trust and proper segmentation techniques, one can reduce the damage done by the mistake of a single user. And we can improve the user’s ability to discern benign emails from malicious ones by for example showing them if they have received an email from someone who they’ve never had a conversation with before, who is simply using a spoofed email address. Or we can have user training to improve tech-literacy, helping them identify “tells” that phishers use.
In one way, the user even being prompted to infect the entire domain is a failing of company security and policy, not the user.
The goal should always be to educate, not berate. And that goes beyond phishing and users – educate your fellow member of the information security scene. If our goal truly is to ensure the security of information, we have focus on the cybersecurity hygiene that Microsoft outlined in their defense report – 98% of attacks could be mitigated with basics security hygiene.
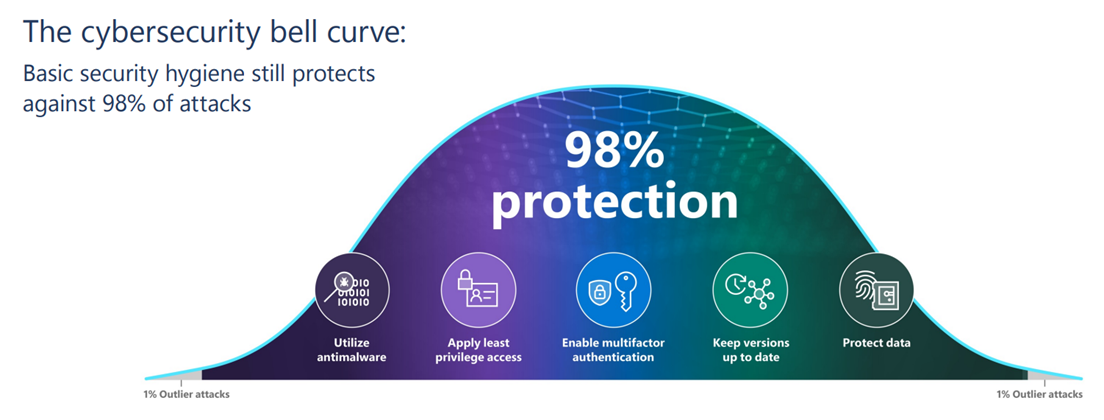
Figure 2: The Cybersecurity bell curve Source: Microsoft Digital Defense Report
A shift in approach and focus is needed on numerous workplaces – a shift away from elitism and highly sophisticated theoretical attacks, and towards the users, and how changes can be implemented to have a practical effect.
For more information, read our blog post on Microsoft Digital Defense Report - A summary.

