MEM, Windows 10 Personal device and Sync issues
In a project lately we use Windows 10 Personal devices that enroll into Intune. Works great, but…. When we configured Conditional Access even if the device is compliant it still blocks access since more Work accounts are configured on the device. On the personal device in this scenario a personal Microsoft Account is used to logon to the device.
Looking under Access work or School under Settings we have more than one account. On an Azure AD Joined device this works just fine, but in a Personal device you cannot add more than one work account using settings that is.

If we try to add an account from settings, we get this error.
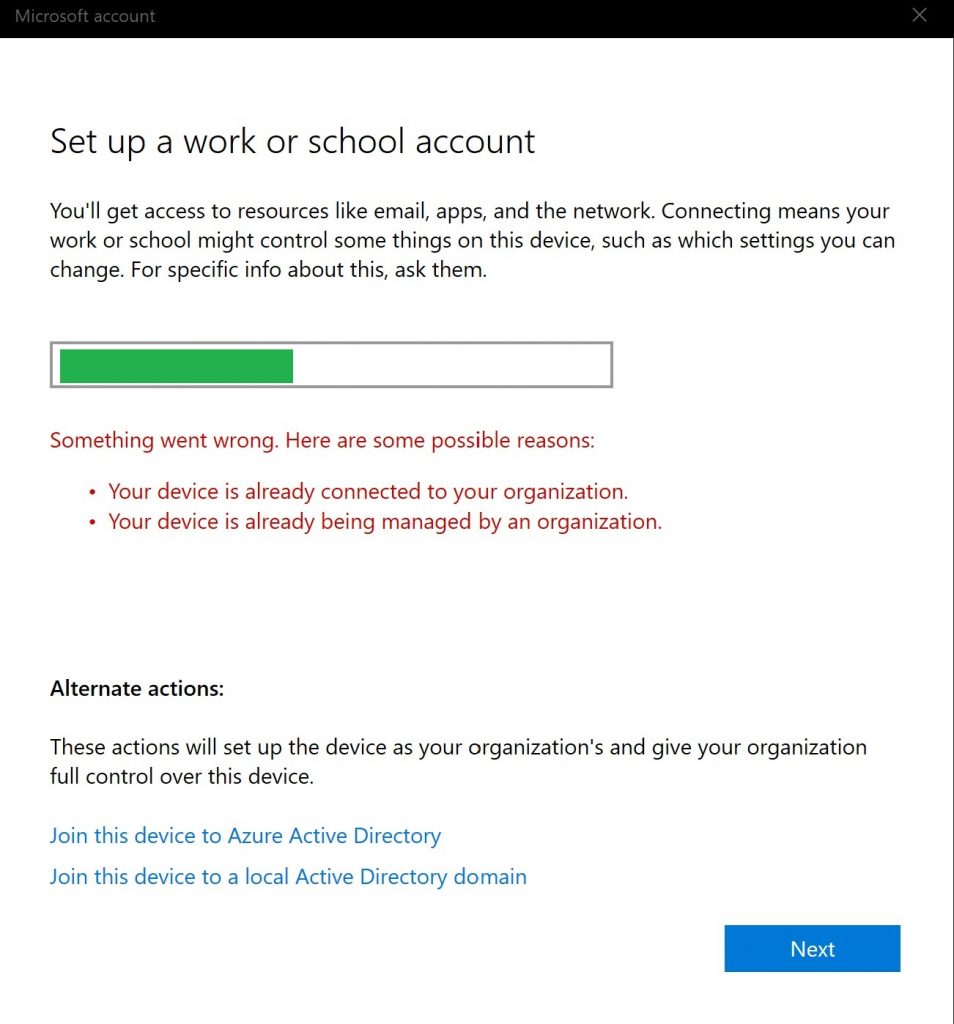
How was the second account added then? Well Outlook is the “bad” app in this case. When you add a second account in Outlook you get this question.

And how many end-users actually select “No, sign in to this app only”???
What happens when a second account is added, which is blocked for a reason in Windows? Synchronization with Intune fails.

If we look in the Event log, we find the following error.
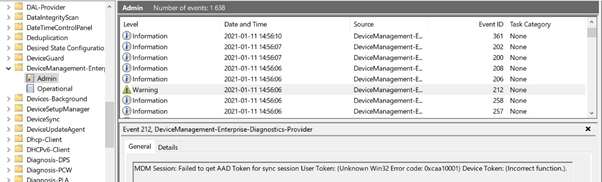
It seems like there is a reason that Windows 10 blocks adding more than one work account.
How can we help the end user making the correct choice in Office?
Well in the same way we do it for an Azure AD Hybrid Joined device, that blocks AAD registration by configuring the following registry value,
HKLM\SOFTWARE\Policies\Microsoft\Windows\WorkplaceJoin: “BlockAADWorkplaceJoin”=dword:00000001
Here is a simple PowerShell Script that we can deploy using MEM to the devices. Then the end user does not get the choice to register the device anymore from Office apps.
$Location = 'hklm:\SOFTWARE\Policies\Microsoft\Windows\WorkplaceJoin'
if ( !(Test-Path $Location) ) {
New-item -path $Location
New-ItemProperty -Path $Location -Name "BlockAADWorkplaceJoin" -PropertyType Dword -Value "1"
}
We create a Dynamic Azure AD group which will include all our enrolled Personal Windows 10 devices, which we can use to target the PowerShell script.
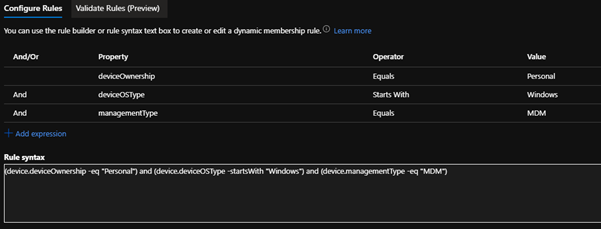
Rule syntax:
(device.deviceOwnership -eq "Personal") and (device.deviceOSType -startsWith "Windows") and (device.managementType -eq "MDM")
Upside, happier end-users, less support calls.
Downside, well as the device is personal and the end-user wants to restore the functionality to register the AAD device, the registry key needs to be removed.
More information about the setting can be found here: https://docs.microsoft.com/en-us/azure/active-directory/devices/hybrid-azuread-join-plan#handling-devices-with-azure-ad-registered-state


