
MFA – necessary but not enough
With the rise of successful attacks against identities, there are a lot of discussions right now talking about Multi-Factor Authentication. Using any type of MFA, especially on accounts with high privileges, is an absolute minimum in today’s threat landscape.
But sometimes, MFA is not enough.
Have I got your attention? Good 😊
But let us start with the basics…

Why are passwords bad?
“The only ones who like passwords are bad guys!”
We are used to usernames and passwords today. It has been the main method of authentication for decades. But using passwords is not a great method to prove who you are. It is hard for users to remember and type, and relatively easy for bad guys to bypass.
Here are just some examples of attack methods against passwords:
- Credential Stuffing
Stealing passwords from less secure systems and trying them on other systems. - Phishing / Social Engineering
Tricking the user into giving away the password. See below for a link to a demonstration video of this. - Keyloggers
Captures passwords as they are being typed. Can be hardware or software based. - Malware
If a bad guy is able to run software on your machine, there are multiple ways to steal your password. - Shoulder surfing
Simply looking while you type your password. - Post-it
Steal passwords that are written down. Hiding the note in a drawer or under the keyboard doesn’t really help. Can also be digital, like txt.
One important key takeaway from all these password attacks is:
"The quality of your password does not matter. At all!"
Since the bad guy will get the entire password in these attacks, mitigations like length and complexity do not help at all. So how can we improve the security of sign ins besides passwords? Well, we can add a second factor.
Combining password with something else
A password is something you know. But if we add something you have or something you are, we could block bad guys even if they have gotten their hands on our passwords.
Something you have used to be a separate dongle that you needed to read a code from.

But nowadays it is much more common to reuse something you already have: your mobile phone.
Something you are used to be limited to fingerprint, but now facial recognition is becoming more prevalent on both phones and computers.
 By combining password with something else we get what is called Multifactor Authentication (MFA).
By combining password with something else we get what is called Multifactor Authentication (MFA).
By using MFA, you are stopping more than 99% of identity-based attacks today. That is not just some marketing estimates, this is actual numbers based on actual attacks and what would have stopped them.
So when should I enable MFA? Now!
Many organizations are in the process of deploying MFA but are waiting to solve all scenarios, like in this example:
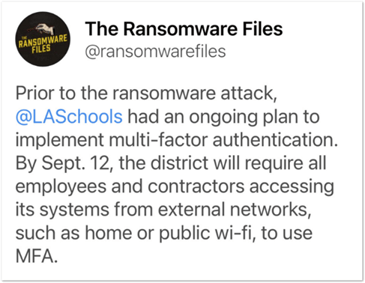
Once companies are “forced” to quickly deploy MFA, it usually turns out that it was quite frictionless for most users.
“You can either enable MFA today, or after the attack.”
If you are not using MFA for everyone today, you should as soon as possible at least require it for your administrative accounts and your most risk-exposed users.
But read the rest of this blog post first since it might affect your method of choice.
Why MFA is not the final solution
When MFA became more popular, the bad guys had to adapt. There are now several attacks against MFA, such as:
- Real-time Phishing
If you can trick the user to visit your site, you can act as an Adversary-In-The-Middle (AiTM) and trick the user into giving away the password. Since they also can steal the session token, even some MFA methods will not stop it.
I recorded a short video demonstrating how this looks for an end user: https://youtu.be/7bOVyEhaCqQ
Would you catch it every time?
- Prompt fatigue
By bombarding users with MFA approval prompts someone will eventually approve it just to stop the constant notifications.
To stop this, you should enable Code Match. Then the user must enter a two-digit number shown on screen and cannot just click Approve/Deny. Microsoft will soon enable this by default for all customers.
- Channel Jacking
If you can take over the channel that the MFA code is sent via, you can intercept the MFA code and take over the account, The most common channel jacking attack is a SIM-jacking, where the bad guy tricks the telecom company to move the targets mobile number to their phone.
This is not just a theoretical attack, Twitter’s founder Jack Dorsey was hit by this, as well as a Bitcoin millionaire, who lost a lot of money.
You should avoid Telecom-based MFA methods if possible, such as SMS and Callback. But also remember that those methods are waaay better than no MFA at all.
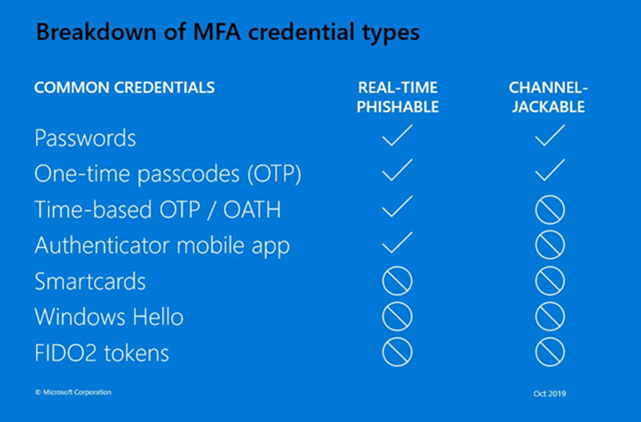
Here is a summary of different MFA methods and their weaknesses:
Going passwordless
Can we get rid of the passwords in our daily work? Yes! At least in most cases.
How it works
With passwords, the user and the service you are signing in to must have the same secret info, to be able to compare the entered and stored password (hopefully salted and hashed, but still based on the same secret).
With passwordless, there is no common shared secret.
- During passwordless enrollment, the user creates a key pair on a device, such as a computer/phone/FIDO2-key, and keeps the private key secret and locked away in hardware
- The non-sensitive public key is sent to the service and mapped to your account
- When you later sign in, the service asks you to digitally sign a random string using your locally stored secret key
- The user returns the digitally signed string (but the secret key is never sent or exposed)
- The service can verifiy that it was signed by the correct private key using the user’s public key
Four methods
Today there are four different passwordless methods. You do not have to decide on one, you can mix and match, so that you can protect most users regardless of their situation.
Windows Hello for Business
This is the easiest and most user friendly for end users. Open your computer, look at it and you are signed in. It does however have some prerequirements on hardware, operating system, and device management.
Note! Do not confuse Windows Hello with Windows Hello for Business.
- Windows Hello is a feature of Windows and technically only a convenience The password is still used by Windows under the covers and can therefore be attacked.
- Windows Hello for Business is an enterprise feature using both Windows and Azure AD. No passwords are involved, only asymmetric keypairs.
Microsoft Authenticator App
Using the Microsoft Authenticator App, you can sign in without a password by simply approving a request on your phone, and then completing face recognition, fingerprint, or the device’s PIN-code.
Most users already have a capable phone that also supports biometrics, so no need to learn something new. It works to authenticate when you are on other platforms than Windows as well.
FIDO2 Security Keys
Security Keys are small, portable, inexpensive devices that enables secure passwordless logon. Perfect for fieldworkers, users that share computers and to use for separate admin accounts.
Certificate Based Authentication (smart cards)
This requires more infrastructure, configuration, and processes than the other methods but is perfect for those organizations that already have smart cards deployed. Now you can use the same smart card to sign into all Azure AD integrated apps as well.
Phishing resistance
To prevent phishing, the user should not be the one who is verifying that you are signing into the right Identity Provider, such as Azure AD. That should be technically verified by the passwordless method itself.
Unfortunately, the Microsoft Authenticator App is not phishing resistant (yet).
Don’t get me wrong, I still recommend it since it increases the security a lot in most other aspects (remember the 99% of attacks that would be stopped by any MFA), but it is good to be aware of this, since your risk acceptance in certain scenarios might affect your choice of method.
This is Microsoft’s current table of MFA methods: 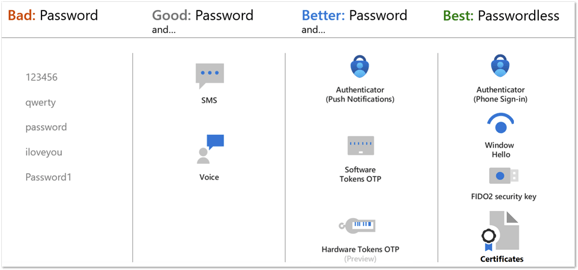
I updated it to add the phishing resistance factor as well:

Do you want to read and or see more:
How to start your passwordless journey (blogpost at onevinn.com)
How to start your Passwordless Journey (webinar at onevinn.com)
Now go and protect your users! 😊


