
Protect and Defend your Identities
As explained in previous posts it becomes even more important to protect your digital identities, both the ones in the cloud as well as the ones on-premises since identity-based attacks are still rising. In the past Microsoft has had two different solutions for this.
Microsoft has now announced the end of mainstream support for one of these solutions, Microsoft Advanced Threat Analytics (ATA) in January 2021. To continue to protect your on-premises identities they have released a guide for moving from Microsoft ATA to the other solution, Defender for Identity (formerly known as Azure Advanced Threat Protection).
But what is Defender for Identity and why is it important to protect your on-premises identities?
Defender for Identity is a cloud-based security solution for hybrid environments. It can be used to identify, detect, and investigate attacks, compromised identities, and malicious insider actions inside your environment by leveraging signals from your on-premises Active Directory. During each phase of the attack it will give you cloud-based insights and intelligence.
Defender for Identity can be used to determine vulnerabilities in configurations and give recommendations for solutions how to solve them. To gain visibility the Identity security posture assessments are integrated with Secure Score.
The Identity Security Posture Assessment helps you understand if an assessment needs you to act on the suggested actions immediately. It helps you focus on what is most important.
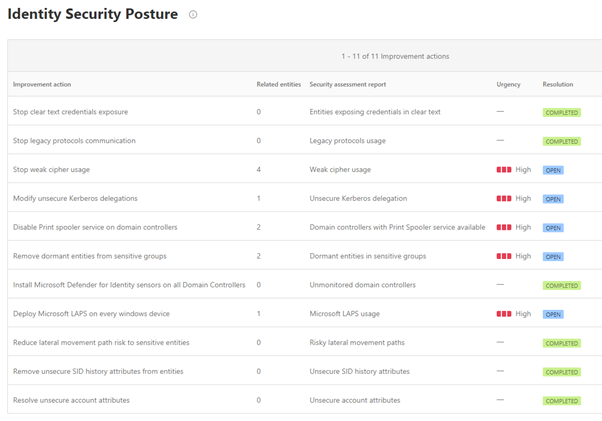
Defender for Identity provides real-time analytics and data intelligence for you to focus on real threats. Microsoft continuously develops new detections which are delivered directly for you to use. These detections/alerts are divided into the different phases of the cyber-attack kill chain:
- Reconnaissance - The phase where the attackers tries to gather information. Different tools are used to get for example, usernames, group memberships, IP addresses etc.
- Compromised credential - The phase where attackers try to compromise credentials using brute force attacks, failed authentications, user group membership changes etc.
- Lateral movement - The phase where attackers tries to move laterally inside your network to gain more access to more privileged accounts using methods such as Pass the Hash, Overpass the Hash, Pass the Ticket etc.
- Domain dominance - The phase where the attackers gain domain dominance, for example by running remote code on a domain controller or using methods such as Golden Ticket activities, malicious domain controller replication, DC Shadow etc.
- Exfiltration - The phase where attackers try to transfer gathered sensitive data to external systems.
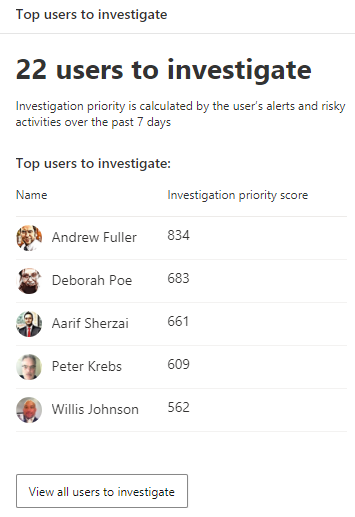
Defender for Identity has a user investigation priority score which can help you to prioritize on the users with most risk. Number of incidents and risky behavior are used to calculate this score. This is done together with Microsoft Cloud App Security where activities on Microsoft and third-party cloud apps are being monitored and risky sign-ins from Azure Active Directory Identity Protection.
Defender for Identity can also be integrated with tools you use today to get automated threat response. You can create hunting queries to find threats in your organization using Microsoft 365 Defender.
The integration with Microsoft 365 Defender and the other Defender solutions is a great advantage and this is explained more in detail in this post.

All together Defender for Identity is a very useful tool for you and your Security Operations team to:
- Stop attacks before they occur by removing on-premises vulnerabilities.
- Understand attacks by supporting Security Operation teams to use their time in the most efficient way.
- Spend their time on real threats and by supporting the Security Operation team prioritizing the information


