
Protect your data from insider risks with Microsoft Purview Insider Risk Management
The biggest fear for the modern organization is that their data leaks and that their sensitive data gets stolen. Many organizations are struggling with how to manage their data because they don’t have a full understanding of the huge risks with manage the data incorrectly. Most data leaks are caused by human mistakes. Example of that is data ex filtering when users decide to use their own solutions instead of the organization provided solutions and it can last for a long time until its noticed. Microsoft 365 Purview have developed a tool to help organizations with this problem and that is Insider Risk Management. It helps to identify and minimize the insider risks to their organization.
Imagine your organization in this scenario, a disgruntled user downloading confidential or secret files from SharePoint or the local network and then leaks it to competing organization or even worse to the public. The user had been planning the leak for months, used personal USB devices without authorization and copying or mailed files to private spaces. This could be a disaster, but organizations can mitigate these risks. Insider Risk Manager can help you identify and prevent these types of malicious activity in quite an easy way.
How it works
Insider Risk Management allows you to easily analyze, detect and investigate the user activity's and also help identify malicious activities, potential risk areas and the type and scope of Insider Risk Management policies you may want to configure. (Figure 1)
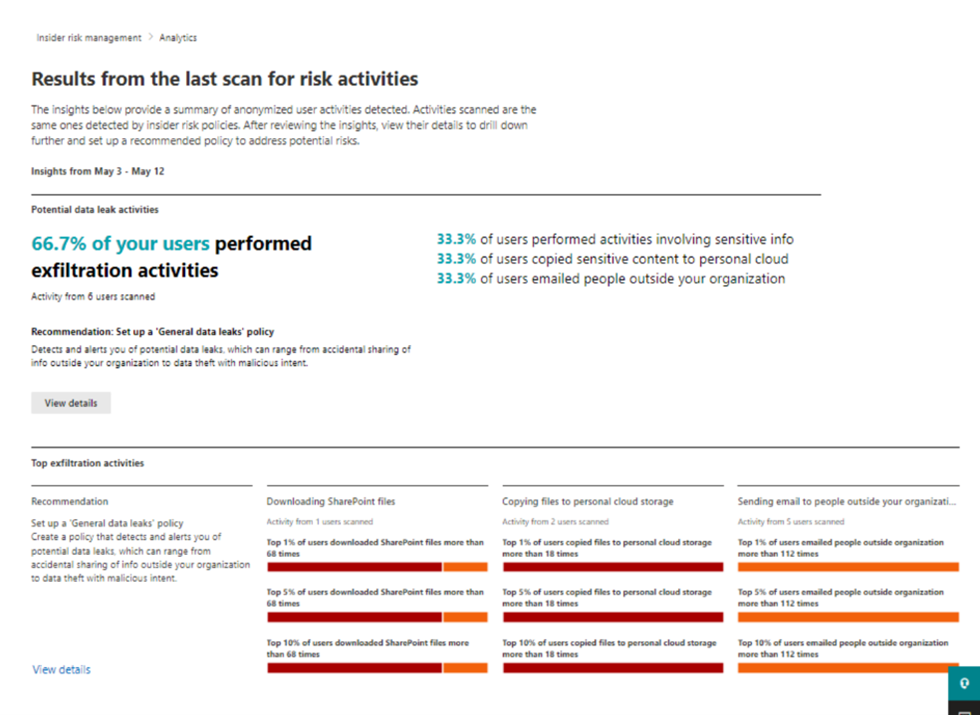
Figure 1
Most policies work best if your organization are using sensitivity labels properly. You can also use Data Connectors to import user and log data from 3rd-party systems that help alert indicators in Insider Risk Management policies. One example is to import human resources (HR) data related to change in a user's job and then be used to generate risk indicators. Data Loss Prevention (DLP) policies are also supported to help identify exposure of sensitive information and are important to get full risk management coverage in your organization.
You can run an analytics scan to search across recent user activity in Microsoft 365 locations and it will show you potential risks, risk scores and help you select a useful policy template such as “Data leak”, “Data Theft” or “Security policy violations” that can be configured to fit your organization’s needs of tracking.
You can choose what specific activities you want to analyze with Triggering events, here are some examples:
- User deleted from Azure AD trigger
- Job level change trigger
- Resignation trigger
Then it’s time to select the indicators that you want to use to analyze and what apps and devices to analyze. Some of these indicators are:
- Delete sensitivity label
- Copy files to USB drives or unsanctioned cloud storages
- Print sensitive files
- Delete files
- Unusual number of downloads
The results will be shown in an easy-to-use overview that allows analysts and investigators to dig into the collected data and start a case, review the cases or the individually alerts that are ranked in severity levels: Low, Medium and High. (See Figure 2)
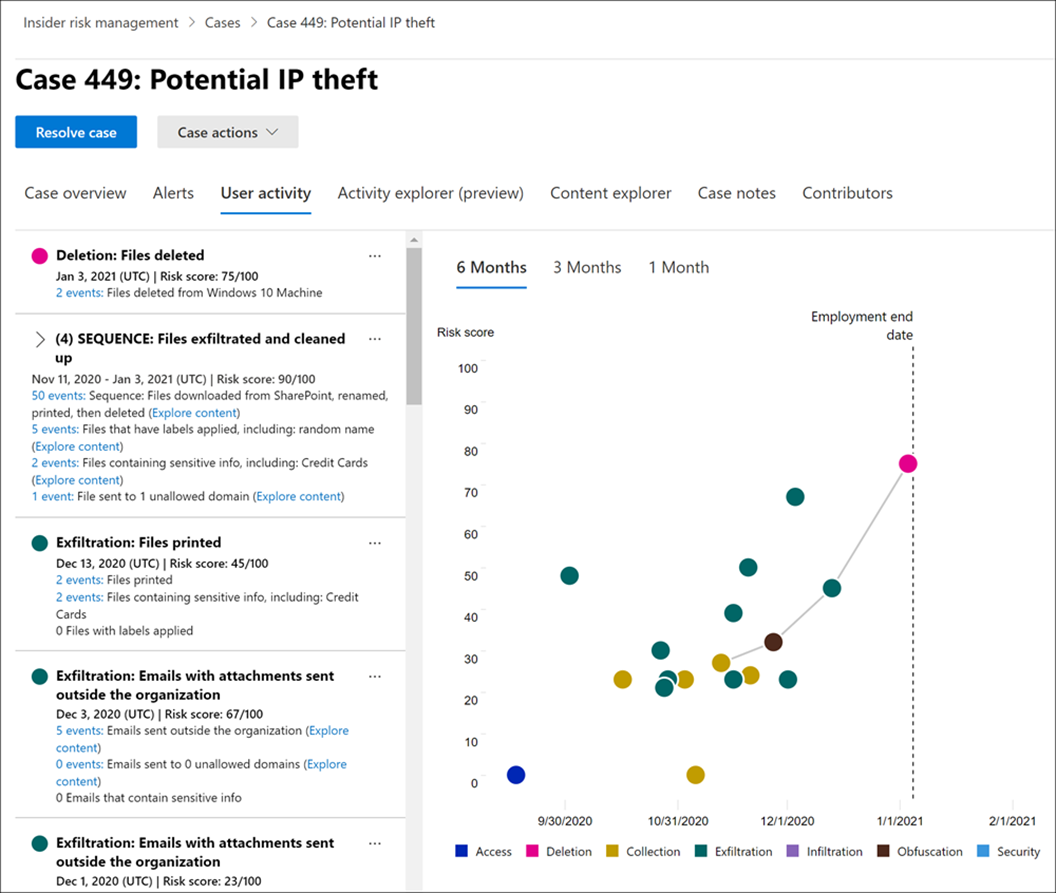
Figure 2
Risk analysts can easily act on and escalate cases in Microsoft eDiscovery. To help meet privacy standards all usernames are by default anonymized (See Figure 3), this can be turned off in settings by some roles and are always getting logged in the Audit section.
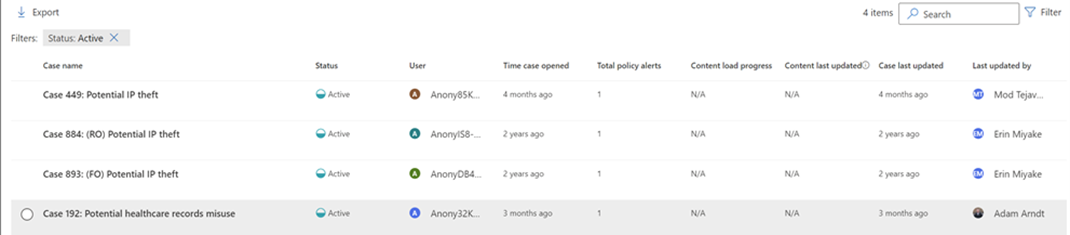
Figure 3
How to get started
When you are going to use Insider Risk Manager, you need to have an existing Microsoft 365 Enterprise E5 subscription and use the role “Insider Risk Management Admin”. If you later are going to start an investigation in eDiscovery you need the “Insider Risk Management” role.
Everything is done from Microsoft Purview Compliance portal. When a policy being created, you define the conditions and indicators that should be used. To mitigate the scenario above, you can choose “Data leaks” and then specify users/groups, SharePoint sites, “Sensitive info” types and “Sensitive labels” to analyze. Triggers for policies can be specified by yourself or use a “Data Loss Prevention” (DLP) policy. (See Figure 4)
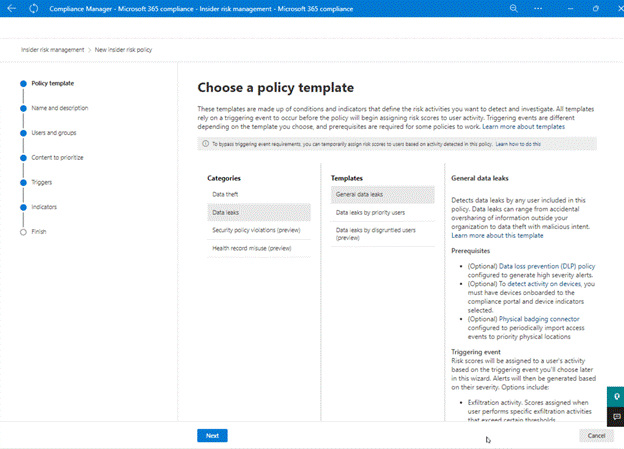
Figure 4
When you have a working policy ready. You need to start the “Scoring activity for users” to get some data to analyze.
After 24 hours you would see new results if users triggered some alerts and you can go to a detailed view to review the alert and see the exact activity that triggered your policy. As mentioned above it shows only anonymized usernames right now.
If you want to get started and have your information protected and want certified offensive security experts you should contact Onevinn. We will help your organization with information security and additionally introduce an Insider Risk Management solution into your environment.
For more information and to get help for your organization with information security and additionally introduce an Insider Risk Management solution into your environment contact Onevinn.
Read more here -> Insider Risk Management

