Protect your environment by reviewing your applications!
To be able to protect our organization as well as preventing information leakage we not only need to secure our own environment we also need to identify what kind of apps and services that are in use by our users.
Microsoft Defender for Cloud Apps, formerly known as MCAS is a great tool to both get to know what kind of apps that are in use, get more knowledge about the apps as well as blocking unwanted application.
There is two different kind of apps that we can identify with Microsoft Defender for Cloud Apps.
- Cloud Apps used from our network (based on FW/proxy logs) and/or devices (via Defender for Endpoint).
- OAuth apps that integrate with our Azure AD, for instance, to sign in a user and/or access a user’s Microsoft 365 information such as calendar, email, and files.
There are a lot of news coming around OAuth apps, lets save that for a coming blog post and focus on the other type of apps, discovered cloud apps.
The risk of not knowing what 3-party apps that are being used is everything from information leakage to identity theft.
It’s called Shadow IT when users start using unsanctioned services to perform their work. With this tool we can easily identify if this is the case either by identify that large number of users accessing the same unsanctioned app or that a lot of data are transferred to a specific unknown app.
Another security risk that it common is that users reuse their work email adress as well as their password for 3-party solutions. We have seen several cases where a web service has been hacked and credentials stolen from this application have been used to get access to the company.
Microsoft Defender for Cloud Apps have built in alerts that reports both new apps that are being identified for high usage as well as new breaches with apps that are in use by our business. We can also create or own alerts and use Power Automate to get the alert into any destination we want and even take automatic actions.
A major challenge with Microsoft Defender for Cloud Apps is to identify ownership within the organization because this is such a broad product.
If we identify Shadow IT, we need to involve several parts of the organization to review what actions we need to take.
Examples include:
- Make sure that we provide our business with the services they need to do their job.
- Inform and educate how to use sanctioned apps and services
- Once we have identified and informed about a sanctioned solution, we can block the unsanctioned solution.
However, it can be more critical in some cases where we need to act as quickly as possible to prevent information leakage. This assumes that we have a playbook with actions for this type of alerts.
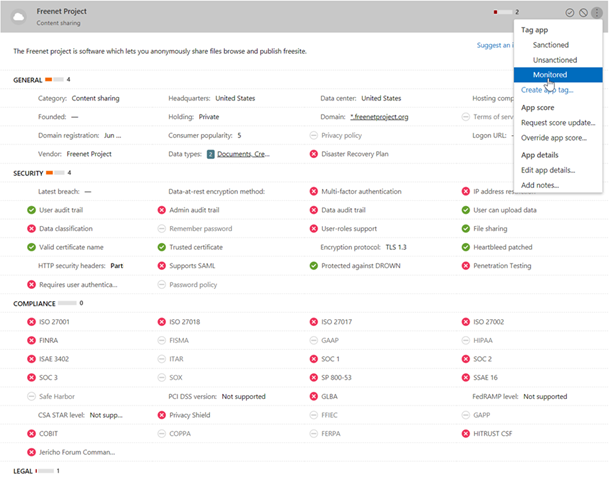
For example, an alarm occurs that large amount of data are uploaded to an unsanctioned cloud app with a low score that turns out to be a service for anonymously sharing information.
A first step that our security operation can take is to start monitoring the service. This results in users being informed that their activities are being logged. If it turns out to be something that is approved by the business, the user can still move on.
A prerequisite to be able to monitor and block the app is that Microsoft Defender for Endpoint is running on the device.
How to get started
If you are working in IT and don’t have the business and its management involved, start by giving them information that Microsoft Defender for Cloud Apps has identified.
One good example as a first introduction for the management is to generate a Cloud Discovery executive report.
Today this is done from the Microsoft Defender for Cloud Apps -portal and the Cloud Discovery part. In a few months this will integrated as a coherent part of the Microsoft 365 Defender portal. Stay tuned for more information around news within Microsoft Defender for Cloud Apps.