Remote Work is Here to Stay
We know that today’s workforce wants to work any time, from anywhere, using their favorite apps on the devices they love.
With Covid-19 striking the world, IT administrators are forced to see an even more mobile workforce accessing the corporate data and we think it is safe to say: Remote Work is Here to Stay!
To handle and manage all these devices it is natural for IT administrators to deploy a Mobile Device Management system such as Microsoft Intune to manage and make an inventory of the devices.
Microsoft Intune can be used to find lost or stolen devices and even wipe only corporate data, leaving personal data untouched. You can also push corporate apps and enforce policies to as an example set passcodes or block certain apps.
Using Microsoft Intune Mobile Application Management allows IT Administrators to restrict corporate data being copied to personal apps.
But is this enough to protect the corporate network and data? With a MDM/EMM you now have control over the configuration of your devices but what about the integrity, behavior and monitoring of the devices? What if a user installs a malicious app? Or a phishing link is clicked on from a mobile device?
For advanced threats you need an extra layer mobile security. Let us go through some reasons why and how the combination of Microsoft Intune and Lookout Mobile Endpoint Security can help you!
Phishing
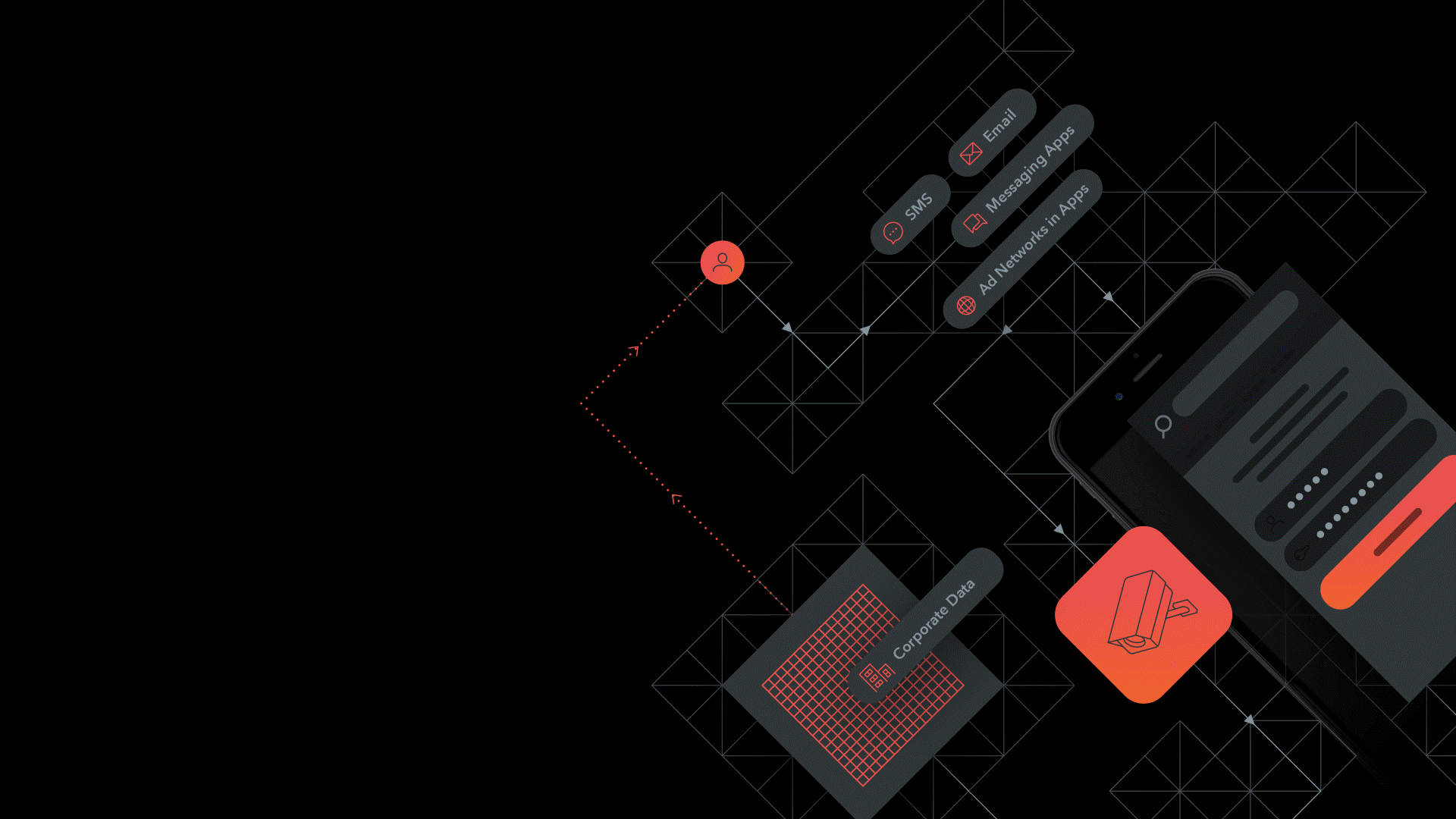
We know that mobile devices are used for both work and personal use. Even if the device is enrolled to the corporate MDM a user can be target by a malicious attack.
The attack vector is just not email, it could be SMS, chat from social media apps or internet-based messaging systems.
Lookout Mobile Phishing Protection is a feature in Lookout Mobile Endpoint Security that can help in the battle against phishing. When the user tries to connect to an URL all outbound connections from the mobile device or apps at the network level are inspected by Lookout. User privacy is not affected since content of messages is not inspected. Lookout Security Cloud keeps track of malicious URL’s and the accessed URL is checked against this and if a malicious URL is detected the user is alerted prior to the connection. This is a real-time alert and prevents exposure against web sites with vulnerabilities or malicious apps. IT Administrators could use the Lookout console to block users who are trying to make connections to malicious URLs that tries to harvest for credentials. Malicious URLs could be link to malware, botnets, spam URLs, spyware etc.
Self-service remediation
Efforts and cost for IT can be reduced when combining Microsoft Intune with Lookout Mobile Endpoint Security. As Lookout Mobile Endpoint Security is available for personal use, as well as corporate use, the interface is easy to understand and does not only alert but also provides detailed instructions on how to remediate. This allows users to self-remediate threats.
Microsoft Intune cannot detect threats alone and therefore end user cannot be notified about threats or guided on how to solve them without additional software.
Realtime Monitoring
Once enrolled into Microsoft Intune, policies can be applied and sanctioned corporate apps deployed. But you still need to monitor the health of the device continuously to keep trusting the device.
Lookout Mobile security is a compliment to Microsoft Intune with its monitoring for phishing, apps, device and network threats.
Lookout can also integrate with Microsoft Intune to restrict access to an app, company resources or network/internet access when a threat is detected.
Even more protection!
Lookout Mobile Endpoint Security provides more protection.
Apps is the most common way to access sensitive data on a mobile device. Lookout’s app analysis technology, which already includes millions of analyzed apps, analyze the installed apps and can give visibility into app-based risks such as:
- Trojans and spyware that can exfiltrate data from the device
- Vulnerabilities in app data transfer and storage
- Risky app behavior that pose a compliance risk
- Side-loaded apps that bypass official app stores
Software vulnerabilities could compromise the device and leading to that the built-in security in the device OS can be bypassed. Lookout security platform tries to identify device-based-risks such as anomalies and risks:
- Behavioral anomalies
- Advanced root or jailbreak
- Out-of-date operating systems
- Device configuration risks
A typical network threat is man-in-the-middle attacks where for example a Wi-Fi hotspot is spoofed in order to intercept network traffic and decrypt sensitive data. Network data is analyzed by Lookout global sensor network Lookout can mitigate false positives and detect network-based risks such as:
- Man-in-the-middle attacks
- Host certificate hijacking
- SSLtrip attacks
- TLS protocol downgrades
So how do we make sure that our users stays safe while promoting remote work?
Watch our recorded webinar


