SCCM integrated MBAM services in Technical Preview 1908.2
Spent last night testing this one out, Microsoft Bitlocker and Managment tool built in SCCM. This is one of the big features me and all my customers are looking forward to! It will make managing MBAM much easier than today by providing:
– MBAM client being part of the SCCM client, so no separate installation and updating anymore
– No additional infrastructure for MBAM, the Management Point role will have the MBAM Recovery and Hardware service.
– Updating the MBAM backend with new Service Releases is not painless today, and now we don’t need to anymore!
– No separate SQL Server/license needed.
MBAM is still the best way to manage your Bitlocker keys today, for having the Recovery keys in a Database separate from Active Directory provides protection against accidental deletion of a computer account and then the Bitlocker recovery key is gone as well. We can cleanup our AD an have it up to date with active clients and still have the recovery keys available if an old computer surfaces that needs to be unlocked.
So how does it work then?
To start with you need to run your Configuration manager site in HTTPS mode.. And it makes sense, do you want to transfer your Bitlocker keys over HTTP?? No, Let’s hope that the released version will Support Enhanced HTTP where self-signed certificates are used.
On the server side we create our MBAM policies under Assets and Compliance\Endpoint Protection\Bitlocker Management
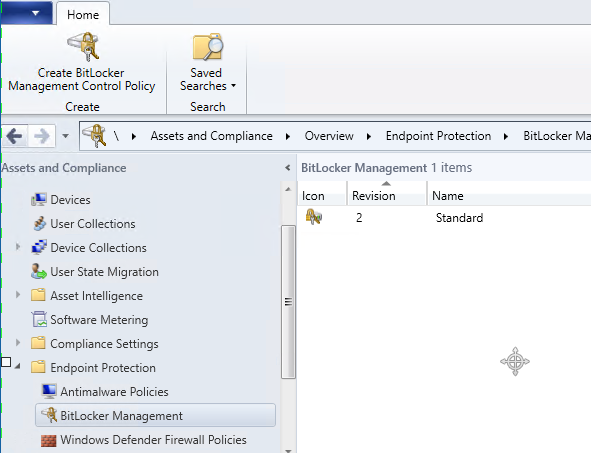
Here we create our MBAM policy, it is the same settings we have in the GPO except for the Reporting endpoint URL is removed.

On the Management Point we have a new Endpoint in IIS (Yes, I had to do some manual steps to get it working). We have an eventlog for troubleshooting as well. So no more updating of the MBAM backend services, Yeah! 😀

On the client and this is really nice:
When the policy is applied to the machine the SCCM client kicks of the installation of the MBAM client automatically from C:\Windows\CCM as shown here in BitlockerManagementHandler.log

There are a second log file on the client as well, BitlockerManagement_GroupPolicyHandler.log which does what it says it applies the settings from the MBAM Bitlocker Policy.

The MBAM eventlog is still there on the client to troubleshoot as well so no difference there.
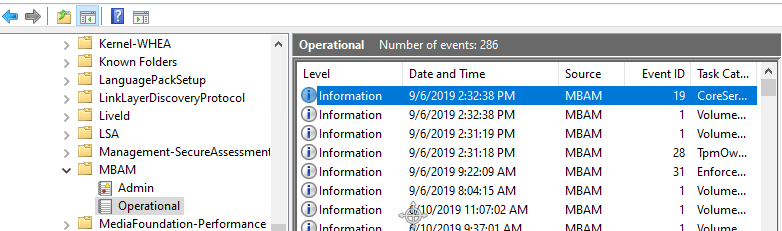
And when the drive is encrypted the recovery keys, user information and computer information is written to the MBAM DB tables in the SCCM Database! No more separate database!

I really want this to be in the 1910 release of Configuration Manager it will make many admins life easier! Some questions are still open like how do we encrypt the disk during OS Deployment? will there be a new self-service portal or not? Time will tell!
If you want to try this out fellow MVP Niall Brady has written an awesome blog post that will save you a lot of time, you can find it here: https://www.windows-noob.com/forums/topic/16726-on-premises-bitlocker-management-using-system-center-configuration-manager/


