Script to make the user which enrolled in AAD a local admin.
When we use AutoPilot with Windows 10 and Intune one of the great benefits is that we can make the enrolling user a standard user and not local admin per default. In some case we of course need to make the users who enrolled the PC a local admin, perhaps after ordering it from a self-service solution.
This script can be run as a script from Intune, it reads which user enrolled the Windows 10 device from the following registry location.
HKLM:/SYSTEM/CurrentControlSet/Control/CloudDomainJoin/JoinInfo

Then we use that information to add the user to the local administrators group. A very simple way to make the user local administrator on the device.
Adding the computer to the Azure AD group we deploy the script to will make the job done!
The script can be downloaded here: https://github.com/Ccmexec/Intune-MEM/tree/master/Make%20Enrolled%20user%20local%20admin
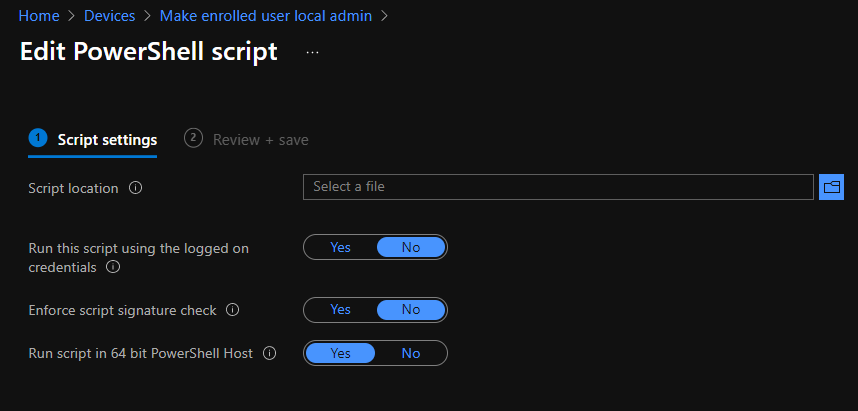
We then add it to Intune as a script with the following settings, note that the script must be run as a 64 bit script as for example “Get-LocalGroup” is not available in 32-bit PowerShell on a 64-bit system.
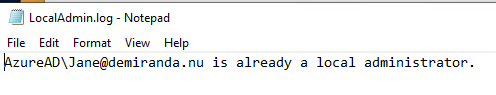
The script will output information to C:\Windows\Temp\localadmin.log, if it is re-run it will check that the user is in the local admin group and output that instead of that is has added the user.
The script works on localized Windows 10 versions, tested on Swedish to make sure. A challenge was that the “Get-localGoupMember” PowerShell command doesn’t work on an AzureAD joined device as there are two unresolved SIDs in the member list. It will throw the following error.
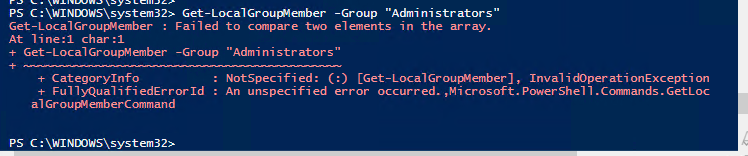
A know issue for a while Get-LocalGroupMember – Failed to compare two elements in the array. · Issue #2996 · PowerShell/PowerShell · GitHub
Here is the script as well:
# Script to update User GPO from System context using a Schedule Task
# Written by Jörgen Nilsson
# ccmexec.com
$LocalAdminGroup = Get-LocalGroup -SID "S-1-5-32-544"
$Localadmingroupname = $LocalAdminGroup.name
function Get-MembersOfGroup {
Param(
[Parameter(Mandatory = $True, Position = 1)]
[string]$GroupName,
[string]$Computer = $env:COMPUTERNAME
)
$membersOfGroup = @()
$ADSIComputer = [ADSI]("WinNT://$Computer,computer")
$group = $ADSIComputer.psbase.children.find("$GroupName", 'Group')
$group.psbase.invoke("members") | ForEach {
$membersOfGroup += $_.GetType().InvokeMember("Name", 'GetProperty', $null, $_, $null)
}
$membersOfGroup
}
# Get the UPN of the user that enrolled the computer to AAD
$AADInfo = Get-Item "HKLM:/SYSTEM/CurrentControlSet/Control/CloudDomainJoin/JoinInfo"
$Localadmins = Get-MembersOfGroup $Localadmingroupname
$guids = $AADInfo.GetSubKeyNames()
foreach ($guid in $guids) {
$guidSubKey = $AADinfo.OpenSubKey($guid);
$UPN = $guidSubKey.GetValue("UserEmail");
}
$Username = $UPN -split ("@")
$Username = $Username[0]
if ($UPN) {
$Success = "Added AzureAD\$UPN as local administrator." | Out-File -FilePath $env:TEMP\LocalAdmin.log
if (!($Localadmins -contains $Username)) {
Add-LocalGroupMember -Group $Localadmingroupname -Member "Azuread\$UPN"
$Success = "Added AzureAD\$UPN as local administrator." | Out-File -FilePath $env:TEMP\LocalAdmin.log
}
else {
$Alreadymember = "AzureAD\$UPN is already a local administrator." | Out-File -FilePath $env:TEMP\LocalAdmin.log
}
}
else {
$Failed = "Failed to find an administrator candidate in registry." | Out-File -FilePath $env:TEMP\LocalAdmin.log
}
I hope you find it useful


