Security summary for Microsoft Teams
We live in a new age around how we work. Even though we see that the Covid pandemic is finally starting to decrease we have created a new way of working. Microsoft Teams have become an increasingly critical service for storage, communication, collaboration both internally and externally. We can see how the utilization rate is increasing more and more by all types of organizations around the world.
During 2022 Microsoft Teams have reached 270 million users worldwide and over one million organizations use Microsoft Teams as the default messaging platform.
This also means that the threats increase at the same rate (just as with other services / platforms that take over the market). If there are large numbers of users and sensitive information, the interest of criminal organizations is increased.
With this article I want to enlighten you what services should be used to face this threat.
The Control panel
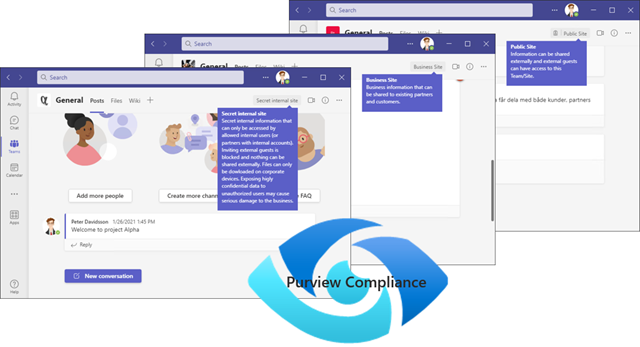
The Microsoft Purview Compliance portal can be seen like a control panel for the Teams platform. With the help of classifications set by sensitivity labels we can design the different Teams and its channels based on the purpose and sensitivity. Controlling everything from guest access, file access, file sharing, to requirements of what users and devices can access and download information.
The key is to make Teams easy to use and understand. After all, the greatest risk of information leakage is our end users. Make it easy to do the right thing and reduce the risk of user mistakes.
Microsoft Purview compliance portal – Microsoft Purview (compliance) | Microsoft Learn
Access and authentication
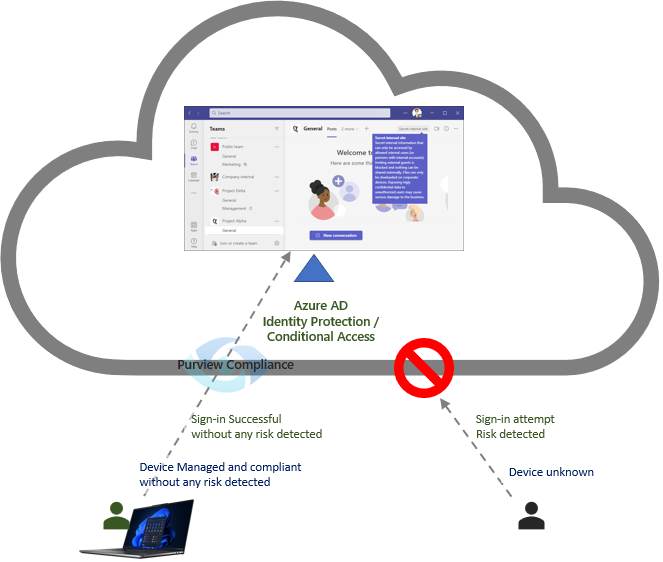
No one has missed that the identity is the new perimeter and that Zero Trust is an important part of designing access. Based on the Teams design we can and should control access with Azure Active directory Conditional access.
-
-
-
- We can define requirements for devices, for example that only company managed devices can get full access to upload/download information.
- We can and should require a strong authentication such as multifactor authentication that has different flavors. We can for example make it easier for the end users with Windows Hello for business or other passwordless solutions.
- Most important of all within true Zero trust, we should always verify the risk of the sign-in, the user and the device. There is no trusted user, device, or network!
With help of the signals from Azure AD Identity Protection and M365 Defender we get both behaviors and reputation -based control. We should regardless of user, device, and network block risky sign-ins both externally and internally.
-
-
One example is to require an internal user to change password directly when it seems to be used by someone else. This automation reduces the time of the breach or completely stops a hijacked account from accessing our information.
Another example is to combine Conditional Access session control with Microsoft Defender for Cloud Apps to monitor and restrict access for non-managed devices. Then we can still allow these devices but prevent sensitive information from being downloaded.
What is Conditional Access in Azure Active Directory? – Microsoft Entra | Microsoft Learn
What is Azure Active Directory Identity Protection? – Microsoft Entra | Microsoft Learn
Files and links
In addition to stolen identities, malicious files and links are still the most common attack route for criminal organizations to get in control of our environments. As our communication paths move from email to Teams, we also see the increase in malicious links and files coming this way.
Microsoft Defender for Office 365 and the built-in virus protection in SharePoint Online provides
-
-
-
- Safe Links protection. URL scanning with rewriting of links and time-of-click verification for URLs within Teams conversations and files. The URL scanning is based on reputation and/or detonation asynchronously in the background. This increases protection against both existing and newly arrived malicious links.
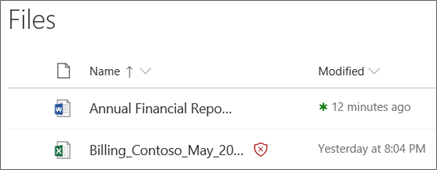
- Virus scanning of uploaded files and virus control during downloading is done by SharePoint Online (that stores all files for MS Teams). Safe Attachments for SharePoint, OneDrive, and Microsoft Teams in Microsoft Defender for Office 365 provides an additional layer of protection for files that have already been scanned. Safe Attachments for Microsoft Teams help detect and block existing files that are identified as malicious in team sites and document libraries.
-
-
Complete Safe Links overview for Microsoft Defender for Office 365 – Office 365 | Microsoft Learn
Built-in virus protection in SharePoint Online, OneDrive, and Microsoft Teams – Office 365 | Microsoft Learn
Information Protection
A potential data breach isn’t the only risk companies face when it comes to unstructured data. Noncompliance with regulations can lead to civil or criminal prosecution for business owners or leaders who are found to be negligent or improperly handling sensitive information.
With help of Microsoft Purview Information, we can
-
-
-
- detect sensitive information
- classify information with purpose for example to define if its public data meant to be spread or sensitive data that should be limited to authorized users.
- restrict sharing and access based on the classification/sensitivity
- encrypt sensitive information. Protection that follows the lifecycle of the information even if it’s allowed to be shared and downloaded. For example, will protected information be monitored even if it´s externally shared and stored outside of Teams and access to the file can be revoked when needed.
-
-
With the help of Data Loss Prevention and Communication compliance we can increase awareness within chat and conversations. Restrict sharing of sensitive information, harassing/threatening language and sharing of adult content that could cause serious damage to our business.
Another example of DLP is to use EndPoint DLP to control what kind of information is allowed to be uploaded to Teams (and other cloud storage solutions).
Microsoft Purview Information Protection – Microsoft Purview (compliance) | Microsoft Learn
Learn about data loss prevention – Microsoft Purview (compliance) | Microsoft Learn
Learn about communication compliance – Microsoft Purview (compliance) | Microsoft Learn
Insider risks
Not only do we have external threats. We can also have internal threats that we need to protect ourselves against. This could be everything from internal users sending sensitive information to their private email with good intent, to someone exfiltrating data with the purpose of leaking trade secrets using an internal user account. Microsoft Purview Insider Risk Management uses the full breadth of service and 3rd-party indicators to help you quickly identify, triage, and act on potentially risky activity. Insider risk management allows you to define specific policies to identify risk indicators. After identifying the risks, you can take action to mitigate these risks, and if necessary open investigation cases and take appropriate legal action.
Insider risk management – Microsoft Purview (compliance) | Microsoft Learn
Data lifecycle management
Microsoft Purview Data lifecycle management is used to comply with laws and regulations. Making sure that irrelevant, out-of-date information is deleted, and that business-critical information is preserved. For example, we can retain or delete certain information based on identified content or the location of the file.
We can also use retention policies and/or a group expiration policy to clean up unused inactive teams/channels and make things cleaner. This makes life easier for our end users and makes it easier for us to protect.
Microsoft 365 group expiration policy | Microsoft Learn
Last words…
Keep in mind that completely blocking external sharing and guests into your organization often leads to increased risk of information leakage. Basically, because sensitive information will be sent by email instead of being stored and shared from your organization. Shadow IT will increase where employees find their own way of cooperation and sharing of information.
Use Microsoft Teams, in a secure and smarter way!