
Threat Hunting
What is threat hunting?
Threat Hunting is, in essence, the act of scouring through data to find something potentially malicious. Malicious indicator generally falls within one of two categories; indicators of attack (IOA), indicators of attacker achievement regardless of exploit used in the attack, a behavior-based indicator, or indicators of compromise (IOC), indicators from a specific used exploit or source IP-address. The efficacy of an organization’s Threat Hunting program is therefore strongly correlated to their ability to aggregate data. Without any data to scour, finding discrepancies or anomalies is therefore far more difficult – or sometimes impossible, depending on the scope and logging capabilities.
Even though Threat Hunting is in essence the same as many detection rules, the intention of the query tends to differ. Some Threat Hunting queries are implemented as detection rules, while others serve more specific purposes, which would risk generating noise if ran on regular intervals.
In brief, a detection rule would be an example of a query you would want to run continuously, while a Threat Hunting query can be expected to generate noise, and the results are not “self-evident”, but may require multiple steps further.
An example of this would be the detection of sign-ins from public IP addresses. While it can certainly be used as a one-time Threat Hunting query, if it’s something the organization would like to know immediately once it occurs, it could be useful to put the query as a detection rule.
On the other hand, detecting all the processes used within a certain time frame would both be vacuous information if used in a detection rule, but would also generate immense amount of noise. Therefore, human expertise, historical data, and proper threat intelligence is paramount for the creation of new detection rules.
Why threat hunting?
While it would be easier to simply automate all queries, as mentioned, the noise simply makes it impractical. Additionally, manual threat hunting has distinct advantages that makes it a worthwhile pursuit compared to automation.
The flexibility of the hunt makes it easily adaptable if something were to be discovered, and the discovery process in and of itself is a boon, as the results are instantly examined by an analyst. Said analyst can then make decisions to adapt the parameters or scope of the hunt, detecting malicious indicators as they go.
That flexibility makes threat hunting an invaluable proactive undertaking which allows companies to scour for threats and issues with a lateral, methodical procedure.
How is threat hunting done?
Threat hunting varies depending on scope and needs, but from a generic security perspective, it’s often utilized when new CVEs or other vulnerabilities are discovered, to scour an organization for them.
As mentioned, threat hunting is divided into two categories: proactive threat hunting and reactive threat hunting. Both methods utilize the following steps, but in different ways:
-
- Collect data: Threat Hunting requires data collection to build a network of entities affected.
- Hypothesis: an idea of the use case and what you want the hunt to accomplish.
- Identify threats: as part of the hunt, you want to be able to identify and segment specific threats, documenting them as you proceed.
- Response: for each threat identified, you want to determine a response action to be taken.
-
- Hypothesis driven: the threat hunt is formulated based on a specific thought or concept, and its scope may creep depending on findings.
- IoC/IoA Driven: a discovered IoA/IoC can drive a threat hunt’s direction, whether if it’s a scope shift as IoAs/IoCs are discovered during a hunt, or if a detection rule detects them and prompts the reactive hunt.
- Advanced Machine-based models: generated by machine-learning and followed through based on its parameters.
Proactive Threat Hunting
Proactive threat hunting is performed for the purpose of scouring for possible cyber-attacks. See figure 1. A plan is formed prior to the engagement, which may be founded on a newly released CVE or newly discovered vulnerability, or for the purpose of discovering undetected IoAs and IoCs (such as scans or commands that dump credentials). The threat hunt is then performed with the specified scope and parameters, hunting proactive for something that may not currently be an active threat, but is a vulnerability, nonetheless.
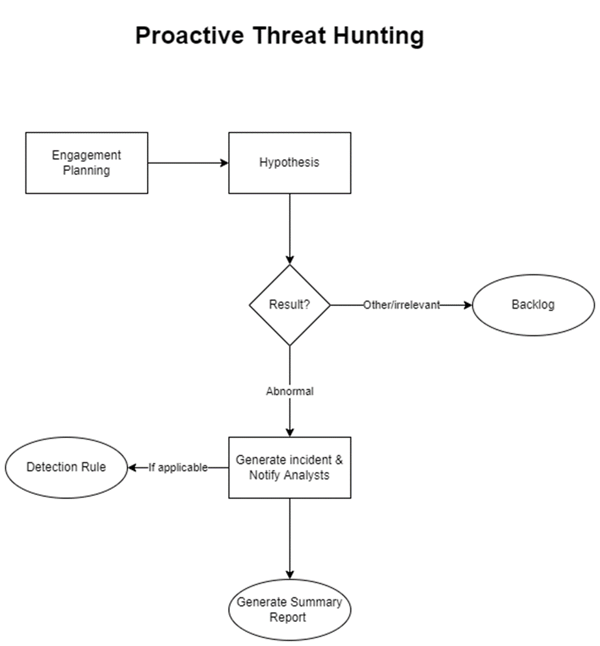
Reactive Threat Hunting
Reactive threat hunting is threat hunting conducted after a security incident is discovered. This type of threat hunting can be conducted in isolation but is often part of the incident response for a certain incident. The purpose of reactive threat hunting is to map out an incident and discover facts related to the incident by finding interesting data about impacted entities, discovering IoCs/IoAs, finding interesting data related to a potential attacker, etcetera. These entities and systems are mapped out to create a full framework of what’s related to the attack, giving analysts a “road map” for what needs to be investigated, and how it connects to other affected entities.
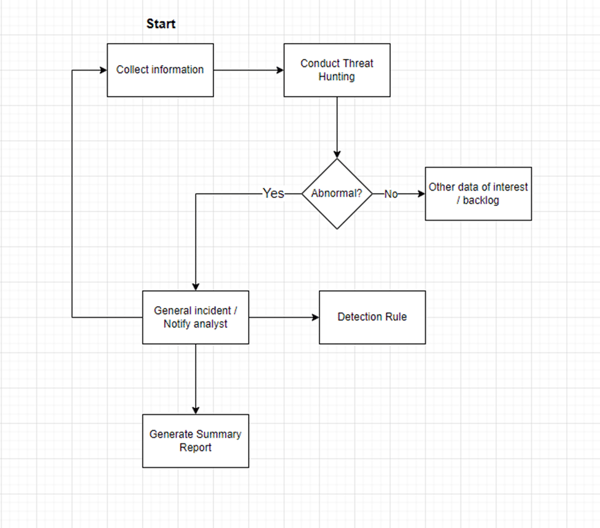
These hunting queries are then later potentially turned into detection rules – often with minor tweaks to minimize noise and mitigate alert fatigue.
Summary
In essence, threat hunting is an essential part of a stable long-term security posture. The proactive hunting seeks to find undetected attacks, and to prevent future attacks from occurring, while reactive hunting mitigates and stops attacks in progress. Both methods are then attuned to the system and tailored for the automated detection of similar incidents immediately as they occur, further heightening the security posture of the organization.
Read more about our security services here:
And last but not least: Happy Hunting!

