What is Microsoft Entra Private Access?
How to modernize and secure access to private apps and resources with Microsoft Entra Private Access
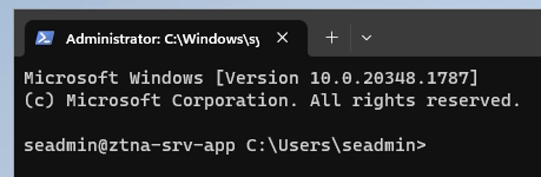
On July 11, 2023, Microsoft announced, among others, Microsoft Entra Private Access as a new member of the Microsoft Entra product family. Together with Internet Access and Defender for Cloud Apps they form Microsoft’s Security Service Edge (SSE) solution, unified under Global Secure Access (GSA) in the Microsoft Entra admin center.
Private Access enables secure and seamless access to private apps and resources - across hybrid and multicloud environments, private networks, and data centers - from any device and any network.
This will enable customers to graduate from legacy VPNs to a Private Access full SSE solution with Zero Trust network access capabilities.
 Links
Links
Microsoft Entra Private Access Preview
Challenges
Hybrid work and accelerated migrations of apps and resources to the cloud is yet again at the forefront of this discussion. More work is being done outside of the traditional network perimeter. Users circumvent IT controls and access resources directly. Hair pinning traffic and routing through headquarter increases network strains and creates sub-optimal user experience.
Legacy network access tools and traditional VPNs have several challenges. They can be complex to manage and operate, often provides excessive access, and have poor hybrid workforce experience. The access is usually user-to-network segment which enables lateral threat movement and reconnaissance.
Background
Azure Active Directory's Application Proxy provides secure remote access to on-premises web applications. It has been around since 2014 with great success and millions of customers. But until now the limitation was always for web applications. Entra Private Access is building on the great foundation and success of the App Proxy enabling you to protect all apps that traverse over TCP and UDP, including RDP, SSH, SMB, FTP.
Security Service Edge (SSE) as the solution
Coined by Gartner in late 2021, SSE focuses more on the security capabilities (such as ZTNA, FWaaS, SWG, CASB), and less on the network connectivity and infrastructure. An entirely new model of networking is needed in which companies connect their end-users and external resources and internal IT systems through a cloud-based platform.
With this model admins can apply advanced access controls to enforce zero trust policies at the very first bastion of access (to network). For instance - identity, device and location checks leveraging Conditional Access. Powerful session controls with Continuous Access Evaluation (CAE) with token revocation on critical events such as account lifecycle and network location changes. This will apply to all/any endpoints, agnostic of native integration within the application or client.
Global Secure Access Client
As of now, the standalone Global Secure Access Client is a prerequisite for connecting to the managed cloud service. Microsoft has announced that the client will be embedded natively in Windows OS in the future. It hooks into the kernel as a lightweight packet filter driver, which also enables co-existence with other first and third-party VPN or SSE solutions.
As for mobile it will be part of the Defender app, acting as the “orchestrator layer”/VPN app where multiple first party services can plug in e.g., Intune tunnel/Defender/GSA to create their own tunnels with respective endpoints.
Flow
An admin defines a set of policies within the GSA control plane. As the client bootstraps it will first receive the traffic forwarding profile (in case of private apps, containing application segments), then triggering authentication against the cloud service. The client will now establish the outer infrastructure gRPC tunnel.
When the user attempts to access resources within scope of a GSA policy, the client would cross reference that access attempt against the traffic profile. If the access is within scope of the policy, the client will ensure that the user has been pre-authenticated and fulfilled Conditional Access - for every flow/private app. The acquired traffic will then flow respectively over gRPC streams. The access is also governed by private applications in Entra ID/AAD.
Summary
At Onevinn we believe that these new Microsoft security solutions and capabilities will bring great value and security to enable your organization to defend your digital assets. The evolution of the modern network perimeter is a great addition, bringing identity-based network access on a per-flow level.
It’s also important to yet again point out that the Entra Private Access solution have a broad application support, meaning - any app, any port, based on TCP/UDP.
The team at Onevinn has actively been a part of the private previews and are ready to help you get started with Microsoft Entra Private Access. Please don’t hesitate to reach out.
Demo
For this demo I’ve chosen the per-app access model which gives more granular security capabilities (in this case Conditional Access) on, as the name suggest, a per-app basis (compared to the VPN-like experience of QuickAccess).
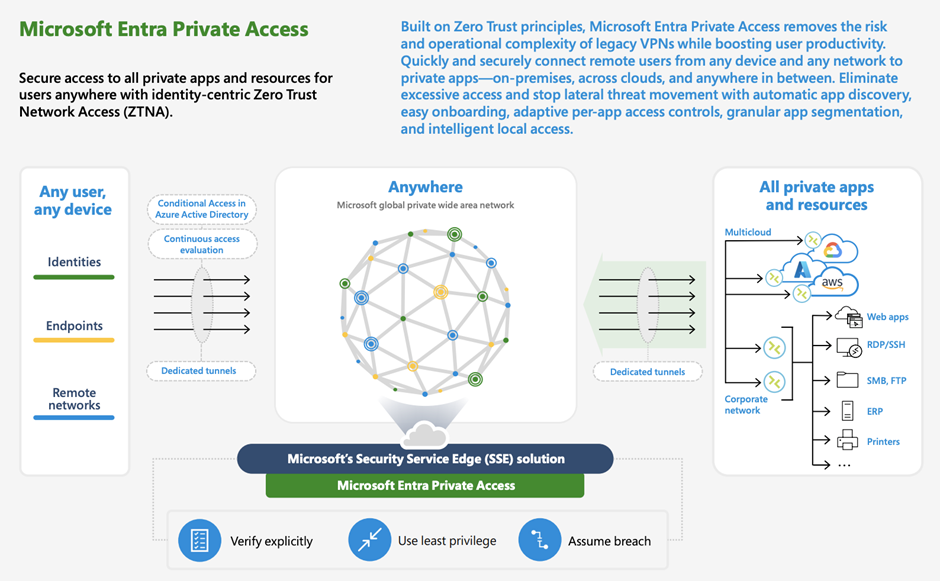
I’ve created a GSA app for SSH, targeting the private IP address of the SSH server on TCP port 22.
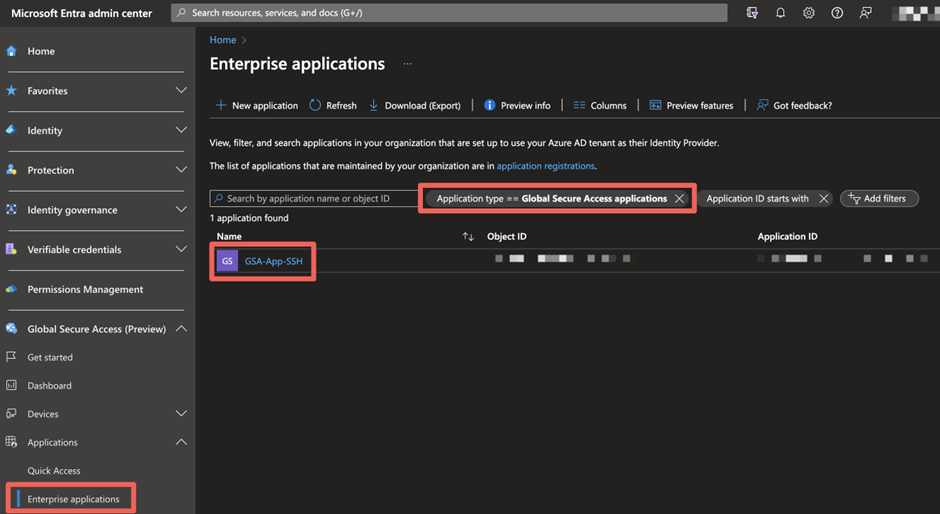
The per-app model lets me pick the newly created GSA app in the Conditional Access policy, which forces an authentication strength.
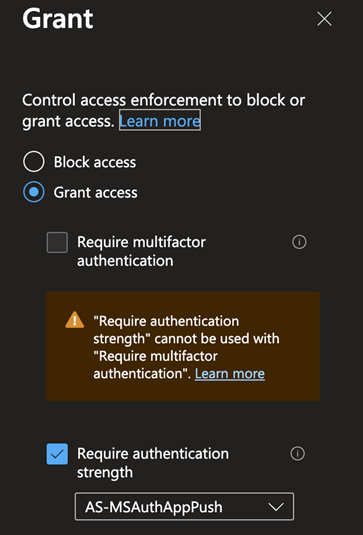
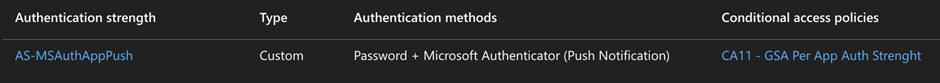
The client has no native network connectivity to the server or line of sight. I’ve also previously only passed MFA with an OATH software tokens, whereas my CA policy requires an authentication strength with the Microsoft Authenticator app.
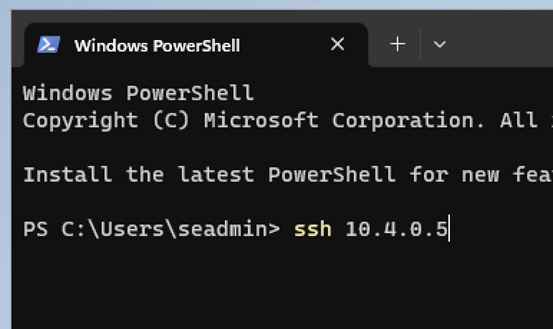
Despite SSH natively having no Conditional Access capabilities, and being a non-web app, I’m presented with the option to pass MFA with the configured auth strength.
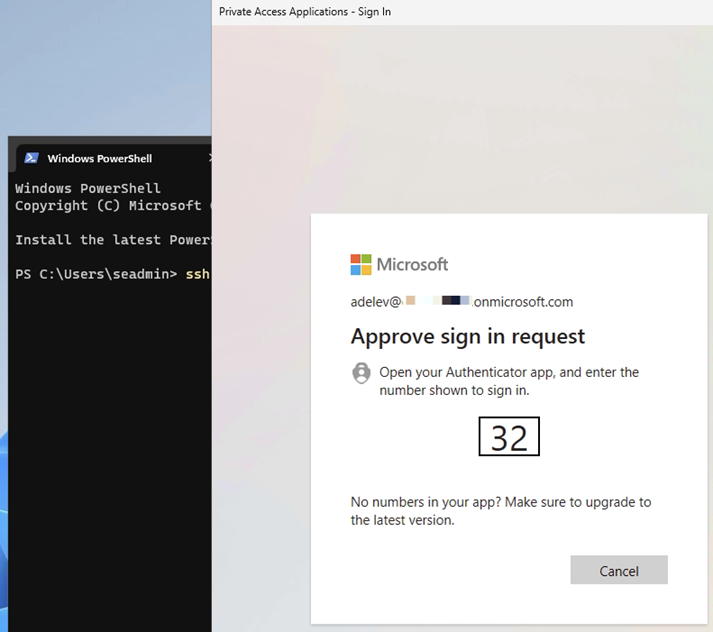
Only after first passing the MFA request am I able to connect and authenticate against the SSH server. SSO would in most cases be preferred, but for demonstration purposes did I configure a policy that would trigger an MFA experience.
Arriving at my destination, SSH access to the server